Are you concerned about the security of your home network and the potential vulnerabilities of internet protocol (IP) cameras? The proliferation of interconnected devices, including IP cameras, has created a landscape where privacy breaches and unauthorized access are increasingly prevalent concerns.
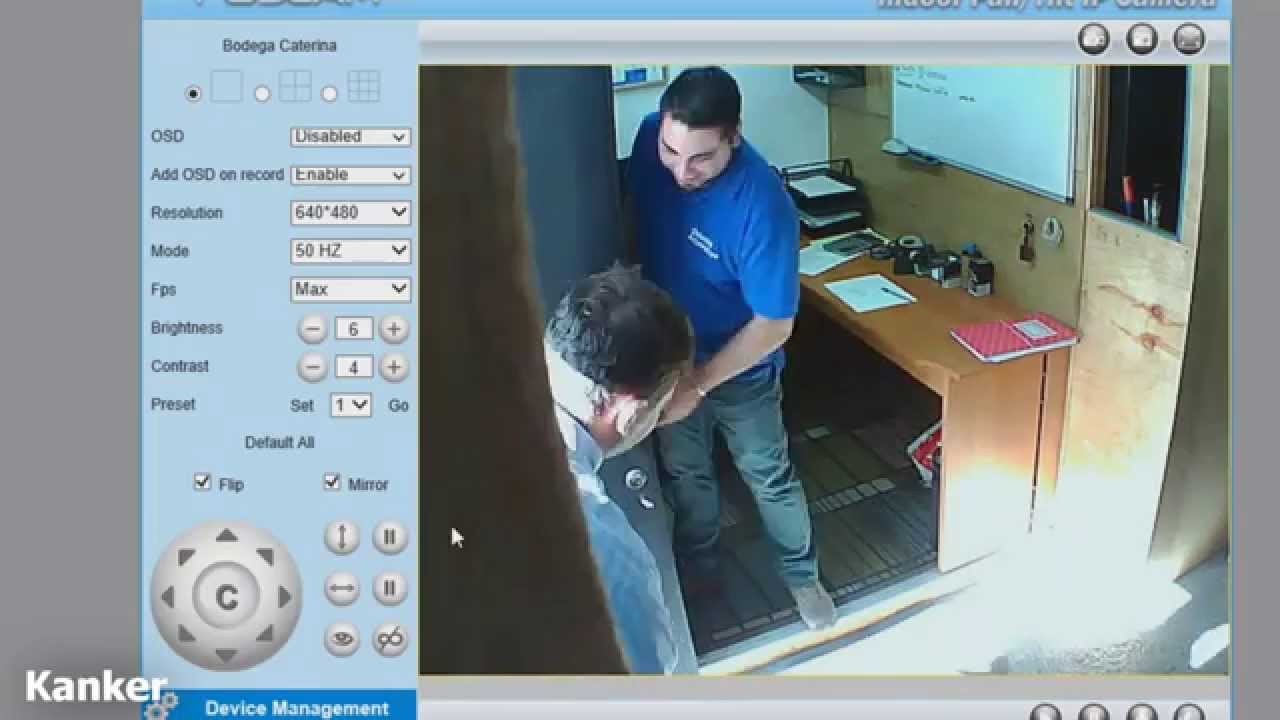
The digital age has ushered in an era of unprecedented connectivity, where devices once isolated are now linked to the internet, offering convenience and new capabilities. Among these innovations are IP cameras, which allow for remote monitoring of homes, businesses, and other locations. These cameras, often marketed as tools for security and peace of mind, have become ubiquitous, found in homes, offices, and public spaces. However, their widespread adoption has brought with it a dark side: the potential for security breaches and privacy violations. The very features that make IP cameras convenient their internet connectivity and remote accessibility also render them vulnerable to hacking and unauthorized access. This creates a complex interplay between technological advancement, security considerations, and the protection of personal privacy. The ease with which a network can be accessed, and the relatively weak security measures often implemented in IP cameras, make them a target for malicious actors. Compromised cameras can be used for surveillance, data theft, or even the distribution of harmful content, underscoring the need for vigilance and informed action to protect against these threats.
The world of IP cameras and the various online platforms that facilitate their use is a complex ecosystem. Many users seek out these platforms, often through search engines or social media, looking for various types of content, ranging from monitoring personal property to accessing entertainment. The nature of this content can vary significantly, with some users looking for legitimate security solutions, while others may be seeking more dubious or even illegal material. The discovery and exploitation of vulnerabilities within IP camera systems is a recurring theme, and various actors are involved, from individual hackers to organized groups. The potential for unauthorized access to private spaces, and the resulting risks of surveillance and privacy violations, is an ever-present threat in this digital environment. The use of technologies like the Real-Time Streaming Protocol (RTSP), often employed by IP cameras to transmit video data, also presents potential risks. RTSP streams, if not properly secured, can be intercepted and viewed by unauthorized parties, leading to privacy breaches. Protecting against these threats requires a multi-layered approach, including robust security measures, user awareness, and vigilance against the malicious use of these technologies. The potential for malicious exploitation underlines the need for a comprehensive strategy to secure IP camera systems and protect the privacy of those who use them.
A telegram bot, a type of software application that runs on the Telegram messaging platform, can be a tool for various purposes, including the remote monitoring of IP cameras. Such a bot, written in the Rust programming language, can be set up to fetch a live record from an IP camera using the RTSP protocol. The motivation behind creating such a bot might be as simple as wanting to keep an eye on one's cats while on trips. However, the underlying technology raises several security and privacy concerns. While the intended use may be benign, the same technology could be used for malicious purposes, highlighting the importance of security best practices. These bots can be deployed locally within a network, possibly using an older Android phone through a tool like Termux, which allows running a Linux environment on Android devices. The technical aspects of such a setup are relatively accessible, but the overall security posture is critical. The security of the network and the camera itself is paramount to prevent unauthorized access and data breaches. Understanding the potential vulnerabilities and implementing appropriate security measures is essential to minimize the risk of compromise.
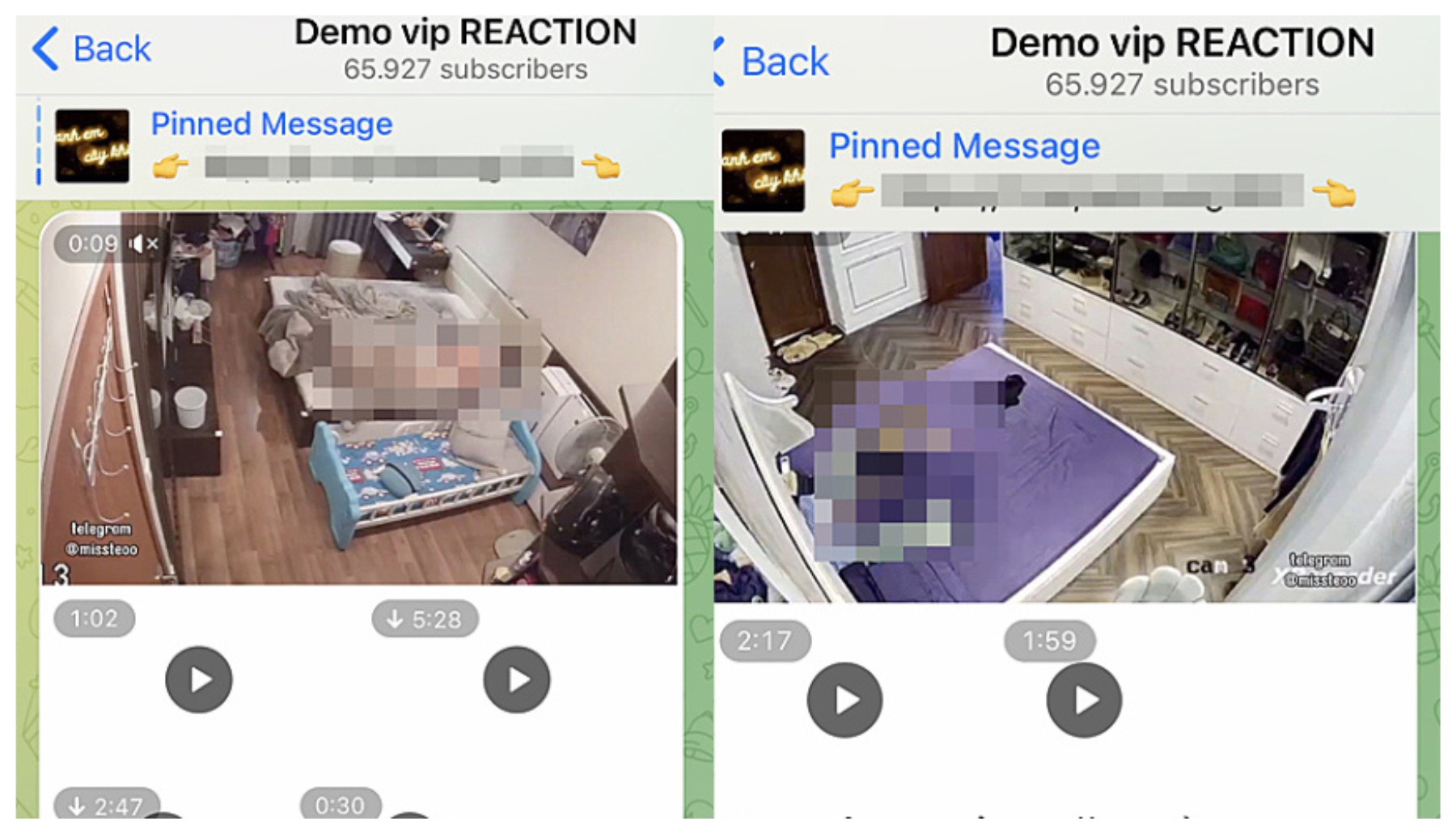
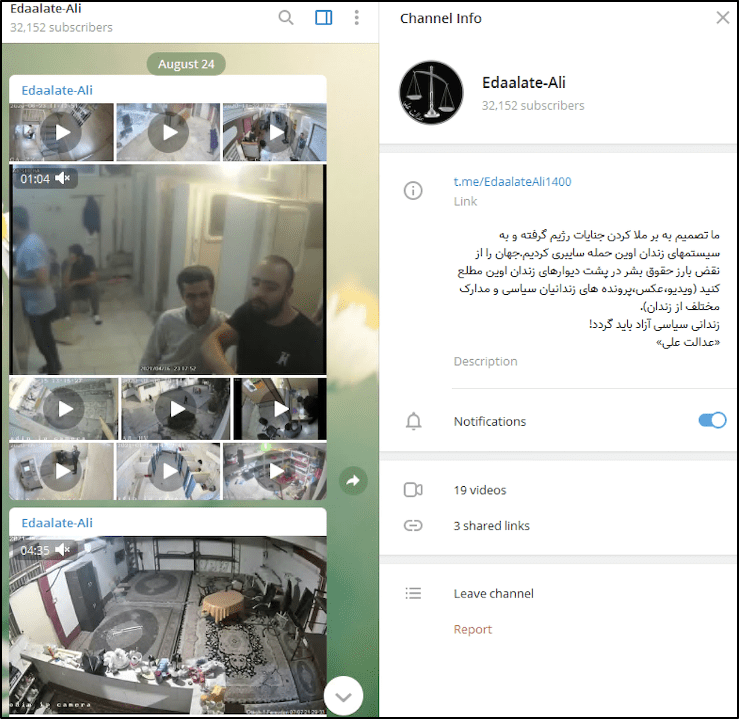
The landscape surrounding IP cameras is filled with a complex mix of legitimate uses and potential for misuse. Various channels and groups exist on platforms like Telegram, some of which focus on the exchange of information related to IP cameras. These channels may offer technical support, share tips and tricks, or discuss security issues. However, the same platforms can be misused to share links to hacked camera feeds or content that violates privacy regulations. Some users seek to access these cameras for voyeuristic purposes, while others might be looking for information on how to secure their own cameras. The duality of the situation underlines the need for awareness and responsible use of these technologies. The Telegram directory, a website that lists Telegram channels and groups, can be a useful resource for discovering these communities. Users can use this directory to search for channels related to IP cameras. However, the presence of channels dedicated to potentially illegal or unethical content should be noted. It is essential to exercise caution and discretion when interacting with such content and to be mindful of the legal and ethical implications.
The technical aspects of IP camera systems involve a combination of hardware and software components. At the core of these systems is the IP camera itself, which captures video and audio data. The camera then transmits this data over a network using protocols like RTSP. These streams can be viewed remotely using various applications, including web browsers or dedicated viewing software. The use of a dynamic domain name service (DDNS) can be used to allow remote access to a camera. DDNS services help keep the IP address updated when it changes. This is often necessary because the IP address assigned to a home network by an internet service provider (ISP) might not be static. If the IP address remains constant, then a much simpler configuration may be possible. The security of these systems depends on various factors, including the strength of the camera's password, the encryption used to protect the data, and the security of the network. Implementing strong security measures is essential to prevent unauthorized access and protect personal privacy.
The rise of interconnected devices, including IP cameras, has led to a growing need for awareness of security and privacy issues. The ease with which IP cameras can be set up and accessed remotely has made them a target for malicious actors. Hacked camera feeds can be used for surveillance, data theft, and the distribution of harmful content. Several communities and forums exist online, often on platforms like Telegram, where users discuss IP cameras. These communities may offer valuable technical support and share tips and tricks. However, the same platforms can be misused to share links to hacked camera feeds or content that violates privacy regulations. Users should exercise caution and discretion when interacting with such content and be mindful of the legal and ethical implications. It is critical to implement strong security measures and stay informed about the latest security threats and best practices to protect personal privacy in an increasingly connected world. Protecting your camera involves strong password and software updates.
The integration of IP cameras into daily life has brought convenience, but it has also raised concerns about privacy and security. The ability to remotely monitor homes, businesses, and public spaces has become commonplace, but the associated risks have become apparent. Several factors contribute to the vulnerability of IP cameras, including weak default passwords, unpatched firmware, and the reliance on internet connectivity. Compromised cameras can be used for a variety of malicious purposes, ranging from simple voyeurism to more sophisticated forms of surveillance and data theft. The sharing of hacked camera feeds on platforms like Telegram is a serious issue that underscores the need for vigilance and responsible use of technology. The use of these technologies must be approached with a strong awareness of their potential risks and with a commitment to implementing robust security measures.
The ongoing discussion surrounding IP cameras often involves the intersection of technology, privacy, and ethical considerations. While these cameras offer a valuable tool for security and monitoring, the potential for misuse remains a constant threat. The presence of channels and groups on platforms like Telegram that share or discuss hacked camera feeds highlights the urgent need for stronger security measures and greater awareness among users. There is the risk of the invasion of privacy and the potential exploitation of sensitive information. Responsible technology use, with a focus on privacy and security, is crucial to mitigating these risks. Implementing strong passwords, keeping software updated, and being cautious about sharing camera access are essential steps in protecting personal privacy.
The ease of accessing and sharing content related to IP cameras, often through online platforms, underlines the significance of responsible technology use. The potential for exploitation and misuse is a real concern, and users must be aware of the risks involved. There are steps you can take to ensure the privacy of your information.
The ecosystem surrounding IP cameras is complex and multifaceted, involving users, manufacturers, and various online platforms. The motivations behind using these cameras can be diverse, ranging from security and convenience to voyeurism and malicious intent. Protecting user privacy and security requires a multi-layered approach, including stronger security measures, user education, and ongoing vigilance. The shared responsibility among users, manufacturers, and platform providers is essential to safeguarding the benefits of IP cameras while mitigating the potential risks.
The evolution of IP camera technology has brought a complex set of challenges and opportunities. As these devices become increasingly integrated into our lives, it is vital to address security and privacy concerns proactively. Strong passwords, regular software updates, and a clear understanding of how the cameras work are essential steps in protecting your information. The balance between convenience and security is an ongoing challenge, and the responsibility lies with users, manufacturers, and platform providers to find effective solutions.
The intersection of IP cameras, the internet, and the various platforms that facilitate their use highlights the importance of digital security and privacy. The potential for unauthorized access, surveillance, and data breaches requires a multi-faceted approach that includes strong security measures, user education, and a commitment to responsible technology use. By understanding the risks and taking proactive steps, users can protect their personal privacy in an increasingly connected world. It is important to stay informed about the latest security threats and best practices to make smart choices for the protection of your privacy.
The content from the original input material is concerning. It includes references to illegal activities, such as accessing and sharing hacked camera feeds, child pornography, and other material that violates privacy. It is crucial to emphasize that any activities that involve the unauthorized access of IP cameras, the sharing of private content, or the distribution of illegal material are strictly prohibited and can lead to severe legal consequences. Respecting the privacy of others and adhering to all applicable laws and regulations is absolutely essential. The information provided here is for educational purposes only and is not an endorsement of or encouragement for any illegal or unethical activity. The potential legal and ethical implications of all actions online must be considered.
| Category | Details |
|---|---|
| Topic | IP Camera Security and Privacy Risks |
| Description | An exploration of the security vulnerabilities of IP cameras, the potential for privacy breaches, and the ethical considerations surrounding their use. |
| Keywords | IP camera, security, privacy, hacking, RTSP, Telegram, surveillance, DDNS, vulnerability, ethical |
| Threats | Unauthorized access, data breaches, surveillance, distribution of illegal content, privacy violations. |
| Technologies Involved | IP cameras, RTSP protocol, DDNS, Telegram, Rust programming language, Termux. |
| Platforms and Channels | Telegram channels and groups related to IP cameras, directory websites. |
| Recommended Measures | Strong passwords, regular software updates, network security, user education, DDNS implementation. |
| Ethical Considerations | Respect for privacy, responsible technology use, adherence to laws and regulations. |
| Legal Risks | Unauthorized access to cameras, sharing of private content, distribution of illegal materials, child pornography, voyeurism. |
| Related Resources | Telegram: https://telegram.org/ |
It is not possible to provide specific details or promote content that violates ethical standards or promotes illegal activities. This article aims to inform users and raise awareness of the risks associated with IP cameras and how they can be mitigated. It is critical to prioritize ethical behavior and adherence to the law in all online activities. Stay informed about these potential security and privacy risks and take steps to protect your personal data.